Native authentication options #
After creation a Cloudlet support both Basic Authentication and JWT token authentication for all API (both Rest and GraphQL) exposed under the Cloudlet path auth.
In the Cloudlets section of the Dashboard, click on the icon in the lower right corner of the Cloudlet panel and choose the Configure option.
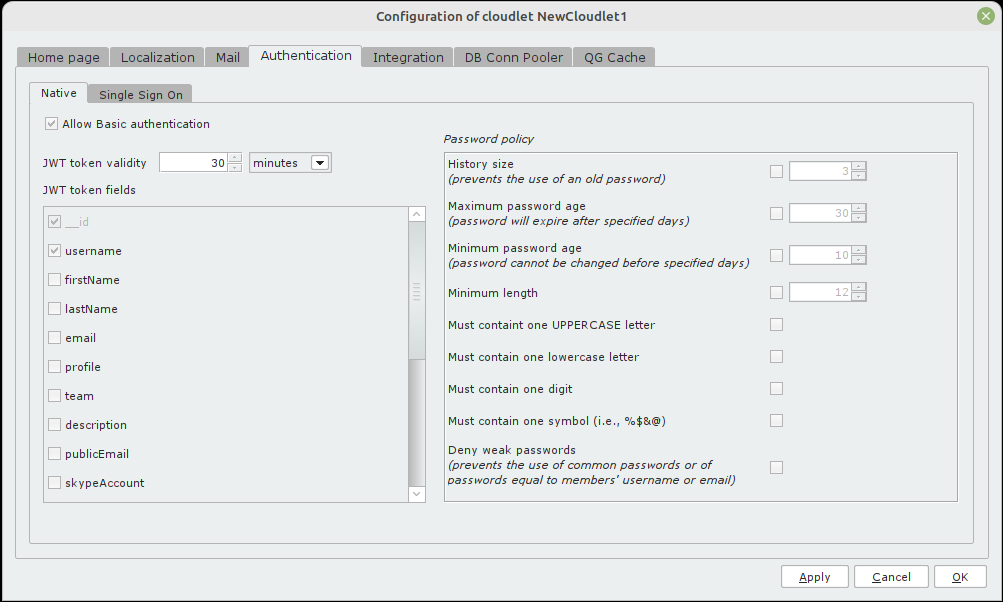
From the Cloudlet configuration panel, click on the Authentication tab and then on the Native tab.
The checkbox Allow Basic authentication toggle the Cloudlet support for Basic Authentication: if no changes have been made, it is enabled by default. If the checkbox is disabled, the Cloudlet will only support authentication via JWT tokens. In this case, any requests made with the Basic Authentication header will receive a 401 Unauthorized response.
JWT Configuration #
JWT Token validity
Determine how long the JWT token is valid from the time of generation: set a number and select the corresponding time unit.
For example, by setting 30 minutes, the token will be valid for 30 minutes from its generation. Once this time has passed, the token will no longer be valid, and any requests made using the token after 30 minutes from its generation will receive a 401 Unauthorized response.
JWT token fields
This section presents all the user attributes that can be added as field to the JWT token.
The __id and username attributes are always added to the token and cannot be deselected.
The username attribute is added as the subject of the token.
Any optional attributes are added to the token as claims only if the user for whom the token is created has a non-null value for the attribute.

Password policy #
In the Password policy section, you can configure the policies for managing user passwords.
History size
The History size field determines the number of unique new passwords that must be associated with a user account before an old password can be reused. Password reuse is an important concern in any organization. Many users want to reuse the same password for their account over a long period of time. The longer the same password is used for a particular account, the greater the chance that an attacker will be able to determine the password through brute force attacks. If users are required to change their password, but they can reuse an old password, the effectiveness of a good password policy is greatly reduced.
Specifying a low number for History size allows users to continually use the same small number of passwords repeatedly. If you don’t also set Minimum password age, users can change their password as many times in a row as necessary to reuse their original password.
Maximum password age
The Maximum password age field determines the period of time (in days) that a password can be used before the system requires the user to change it. You can set passwords to expire after a certain number of days between 1 and 365, or you can specify that passwords never expire by deselecting this option. If a maximum password age is set, then the minimum password age cannot exceed its value.
Minimum password age
The Minimum password age policy field determines the period of time (in days) that a password must be used before the user can change it. You can set a value between 1 and 365 days, or you can allow password changes immediately by deselecting this option. The minimum password age cannot exceed the maximum password age, if the latter is enabled.
Minimum length
The Minimum password length field determines the least number of characters that can make up a password for a user account. You can set a value of between 6 and 255 characters.
Must contain one UPPERCASE letter
If checked, this field requires password to contains at least one UPPERCASE letter (A through Z).
Must contain one lowercase letter
If checked, this field requires password to contains at least one lowercase letter (a through z).
Must contain one digit
If checked, this field requires password to contains at least one base 10 digit (0 through 9).
Must contain one symbol
If checked, this field requires password to contains at least one of the following symbols: %$&@
Deny weak passwords
If checked, this field prevents the use of common password (e.g. “1234”) or of password equal to members’ username or email.

Single Sign-On (SSO) #
Livebase supports integration with Single Sign-On through Keycloak. For more details about the integration, please refer to the page Single Sign-On (SSO).
From the Cloudlet configuration panel, click on the Authentication tab and then on the Single Sign On tab.
Here you can enable the integration with Keycloak by checking the Enable SSO Configuration checkbox.
The Enable SSO Configuration checkbox enables the SSO integration, allowing you to configure the Keycloak integration through the Keycloak Deployment field. For more details on configuring the Keycloak integration, please refer to the page Single Sign-On (SSO)).