Permission Schema #
The schema that allows you to configure the rights that a profile has in a given application is the Permission Schema . Within each Profile Schema there are as many Permission Schema as there are application views to which that profile has access.
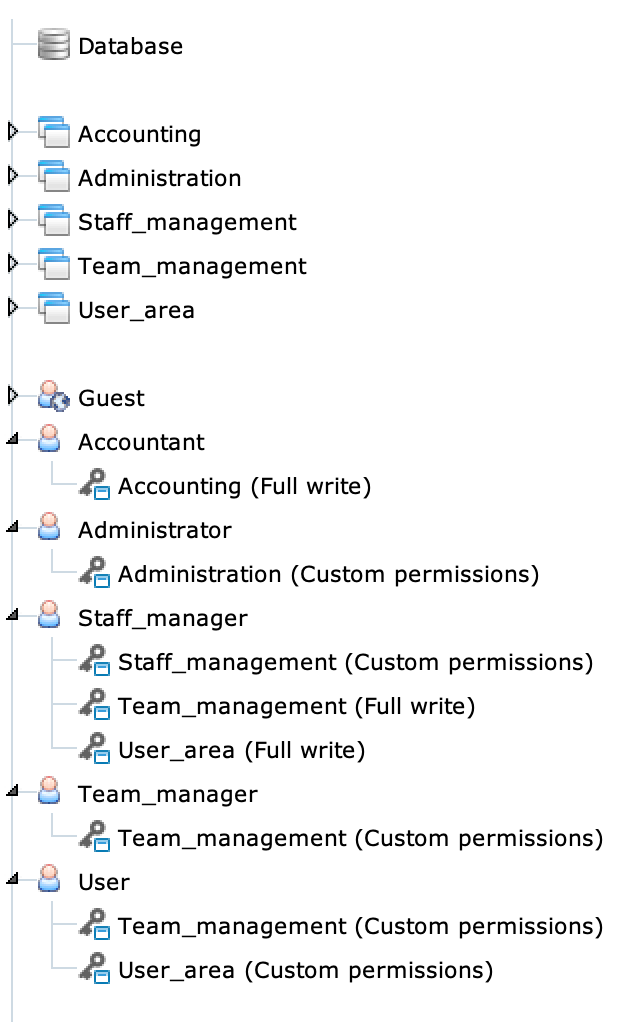
In the above image, you can see how each Permission Schema corresponds to application views assigned to a profile, thus determining permissions on individual elements of the related Application Schema. For example, the Staff manager profile can use the Team management and User area applications with full read and write rights (Full write), while custom permissions (Custom permissions) have been defined on the Staff management application.
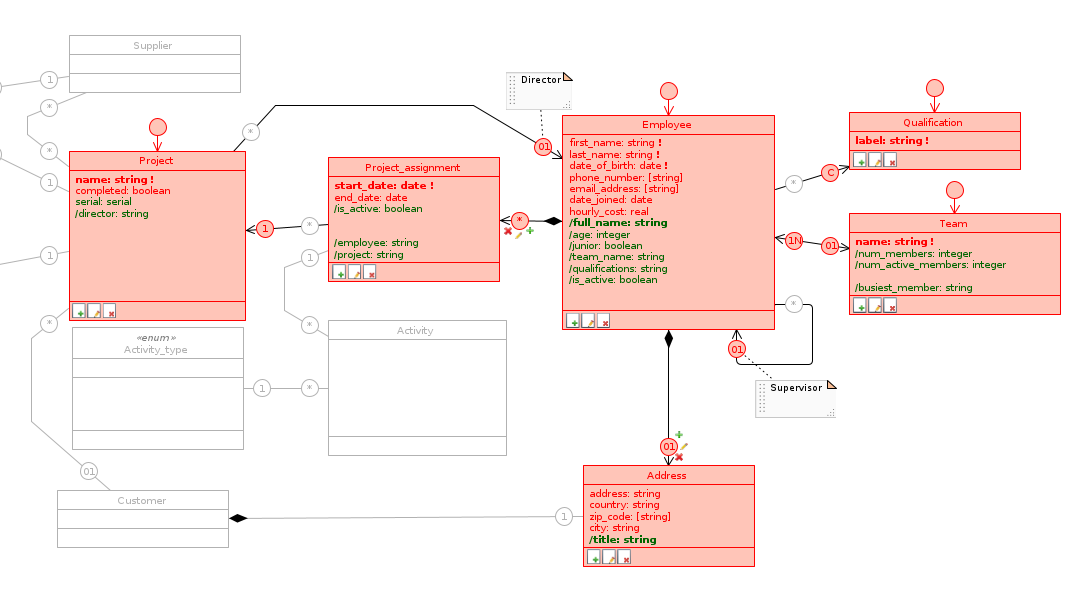
The Permission Schema allows you to view and modify the access type for each class, attribute or relation of the model for the selected Profile Schema on a timely basis.
Just as an Application Schema depends on the Database Schema on which it is defined, a Permission Schema depends on the Application Schema for which it specifies the permissions of that Profile Schema . Therefore, disabled items in the corresponding application view are also disabled in the Permission Schema; in particular, only the gray outline is shown for disabled classes and roles, while disabled attributes do not appear at all and leave blanks in classes.
Each enabled element has three possible states, represented graphically by the following color code:
Modifiable (red): the profile has full access to that element; it can compile it if it’s an attribute and associate objects if it’s a role;
Read only (green) : the profile can see that item, but cannot edit it;
Disabled (grey): not to be confused with the disabled elements inherited from the Application Schema; we can disable diagram elements at this level as well, but always within a single Profile Schema.
![]() By clicking on an element in the diagram we can choose its state among the three configurations just listed.
By clicking on an element in the diagram we can choose its state among the three configurations just listed.
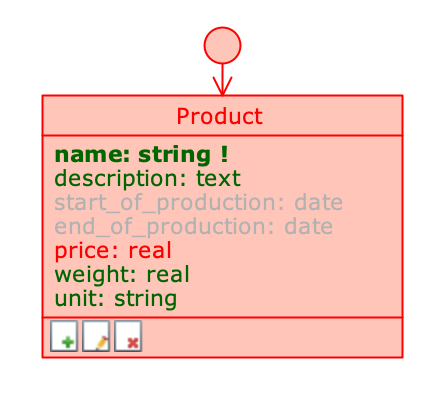
Attributes with different type permissions
The previous image shows a class on which different type permissions have been defined depending on the attribute: the only modifiable attribute is the price (price), while the production start and end dates (start_of_production and end_of_production) are hidden when the application is used by the selected profile.
By clicking on the Default class role of a class, you can quickly scroll through Full write, Read only, or disable it completely.
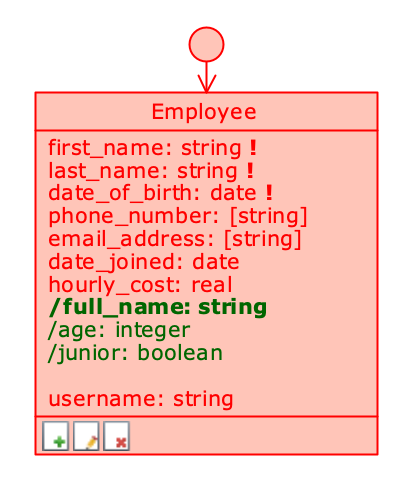
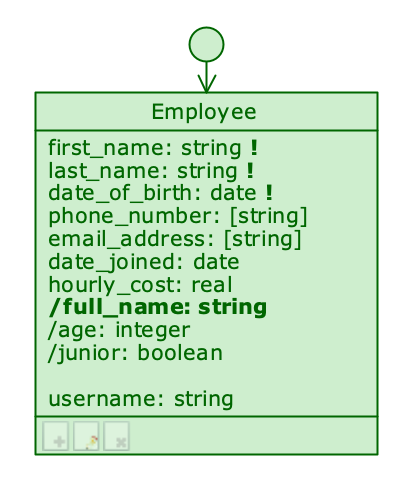
Editable class (with some attributes read-only)
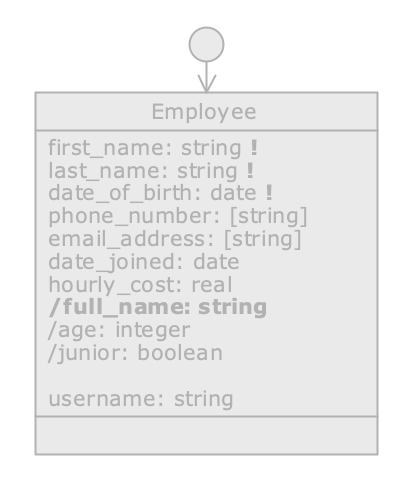
Class with read-only rights
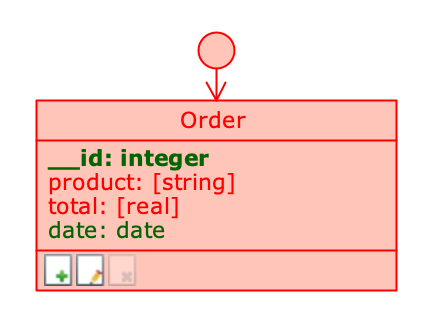
Class disabled in Permission Schema

Class disabled in the Application Schema
If the class is in Read only state, its attributes cannot be modified; this would not make sense, because the class is conceptually at a higher level, and the fact that the profile has no editing rights on it must necessarily apply to its attributes as well. Similarly, if a class is disabled, it is not possible to enable any of its attributes.
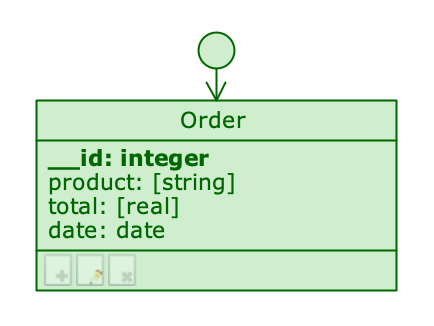
Classes and compositions have an even finer level of detail, represented by three icons in the footer of the class or on the part role:
- represents the right to create new objects;
- represents the right to edit objects;
- represents the right to delete objects.
Modify rights on a class #
By clicking on one of these icons, it is possible to disable or enable the corresponding right; this allows certain combinations of permissions to be set: for example, by disabling only the third icon , a profile will be able to edit objects and create new ones, but will not be able to delete them.
When all three icons are off, and their permissions are disabled, the class and all its attributes automatically switch to Read only mode and appear colored green.
Modify rights on a composition role #
When a composition role is editable, you can set the editing rights in detail, which are graphically represented next to the role itself, as shown in the image:
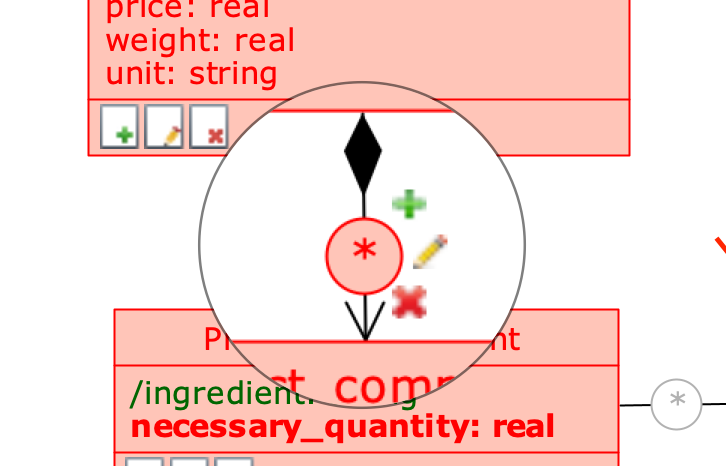
An editable composition role
From the Permission Schema , right-click on the composition role to open its Role menu and check the checkboxes for the rights you want to enable.
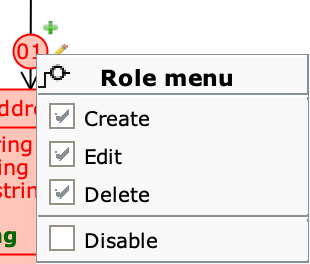
By right-clicking on a role, you can change the rights by clicking directly on the create, edit, and delete icons of the part class. By doing so, in case of part with many whole, all incoming roles of the part class are changed.
General Profile Rights #
It is possible to set the profile rights for an entire application directly from the Settings panel, accessible by clicking on the Profile Schema, and selecting the desired permissions from the drop-down menu that appears next to the checkboxes in the Access to applications section.
The Permission Schema is available for all application views, even those that do not have custom permissions (Custom permissions). For an application view in Full write mode, all enabled items appear in red, while for a view in Read only mode they appear in green.
In the Schemas tab, the label of each schema shows the overall entitlement type.
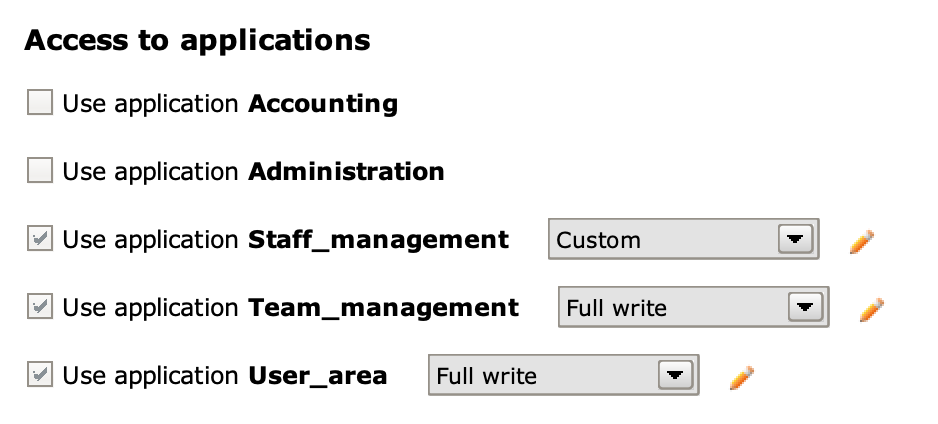
If further changes are made, the permission type (visible in parentheses next to the name of the Permission Schema) will be defined as Custom.
Set default permissions for newly created items #
Right-click on a Permission Schema to open its Application Permissions menu and select the Default permissions on new elements... option from the drop-down menu. Check the desired options from the Application permissions defaults panel.
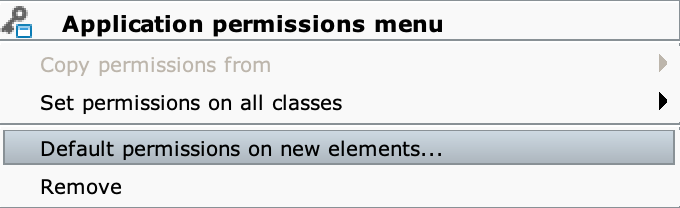
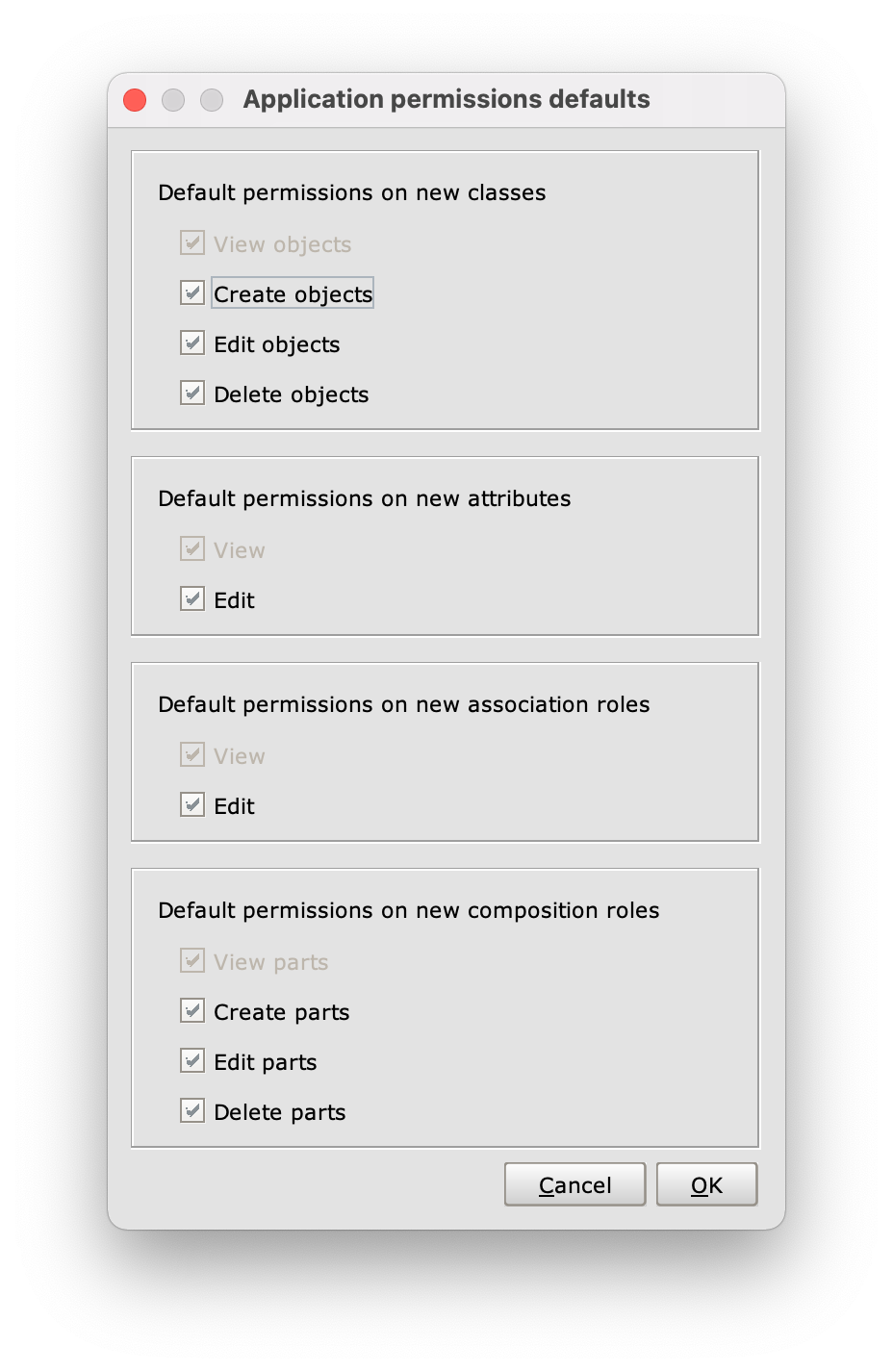
The Application permissions defaults panel
Other aspects of the Settings panel #
From the Settings panel you can configure other general aspects related to profile rights:
- Access to applications: there is a checkbox for each application view in the engine model; when an application view is checked, you can choose the type of access between full (
Full write), read only (Read only) or custom (Custom); - Editing of cloudlet settings: allows you to assign to the profile the right to modify the Cloudlet settings;
- Management of cloudlet members: allows you to assign to the profile the right to create, edit or delete cloudlet members.
When we add a new application view, all existing profiles get access to it. This happens because every application view must have at least one profile that can access it.
Set default permissions for a profile #
Right-click on a Profile Schema to open its Profile menu and select the Profile settings... option from the drop-down menu. Check the desired options from the Profile defaults panel.
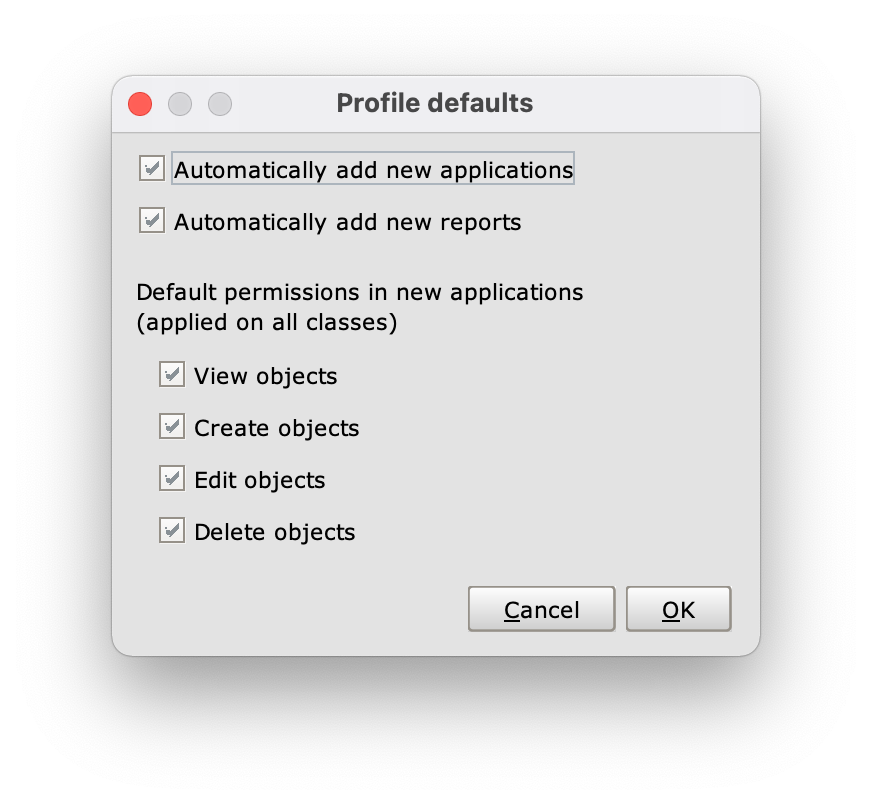
The Profile defaults panel
In the Profile defaults panel, the four options in the Default permissions in new applications (applied on all classes) section allow you to define default permissions for objects in new applications:
- View objects: reading right;
- Create objects: creation right;
- Edit objects: editing right;
- Delete objects: deletion right.
Rights of the __User class #
The rights related to the __User class cannot be changed directly from the Permission Schema but depend on the settings of the Profile Schema Settings panel:
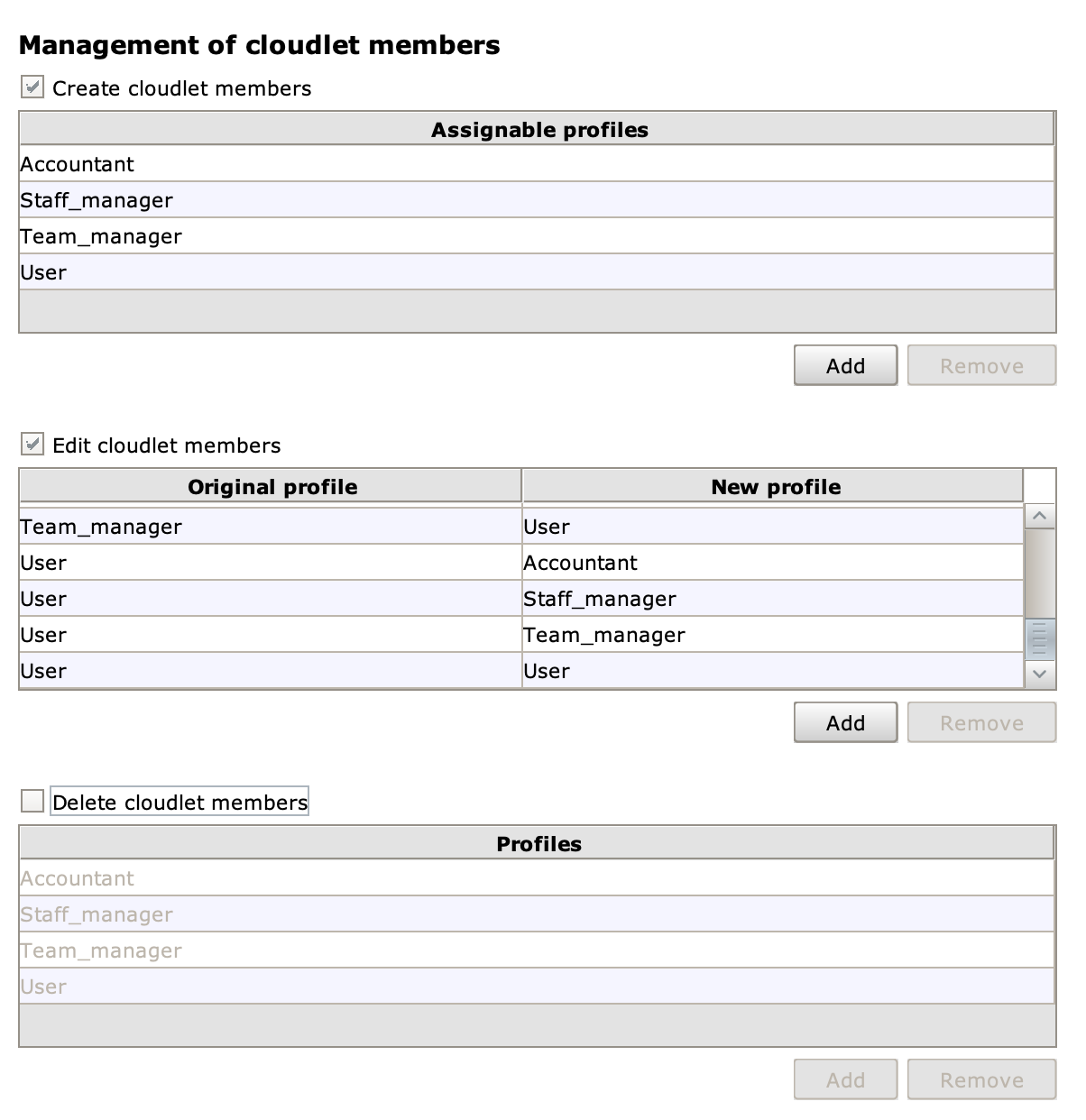
In the Management of Cloudlet members section there are three checkboxes: Create cloudlet members, Edit cloudlet members and Delete cloudlet members, which enable respectively creation, editing and deletion of users whose profiles are listed in the relevant tables.
To grant a particular grant, you must check one of the checkboxes and add the profiles for which that grant is valid by clicking the Add button. To revoke permissions on a previously added profile, you need to select it and click the Remove button.
The Edit cloudlet members table has two columns, Original profile and New profile, and its records represent transitions between profiles; you can edit the attributes of any user whose profile appears in the Original profile column, but you can only edit the profile if the relevant transition is present.
